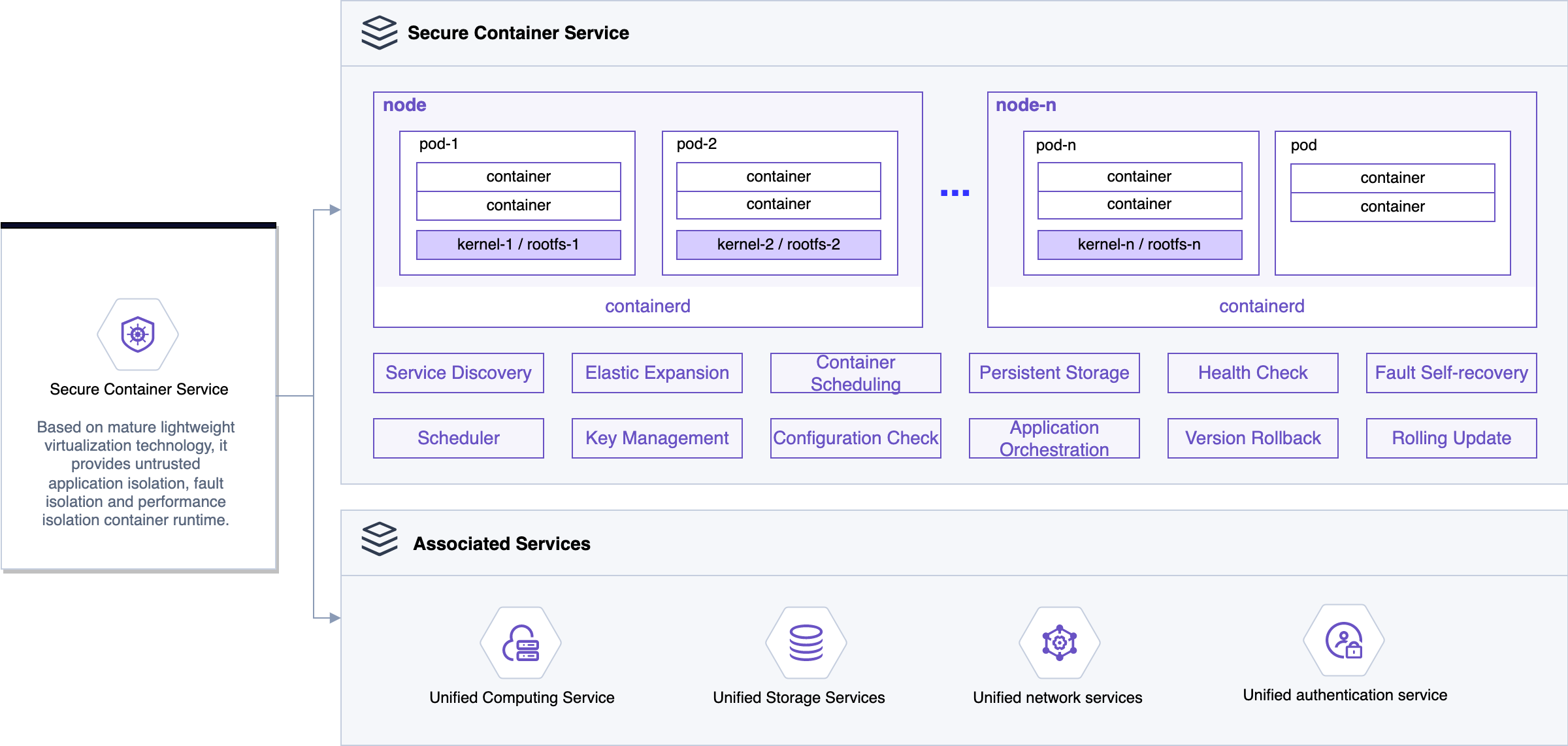
A high-performance, scalable secure container management service. Built on secure sandbox technology, it delivers VM-grade security and resource isolation.
Out of the box
Automated container cluster lifecycle management—from the image you provide to the containers you run.
Strong isolation of resources
Leveraging secure sandboxed container technology, we deliver VM-grade security and resource isolation, while a deeply optimized runtime ensures significantly faster startup times than traditional virtual machines.
Consistent experience, unified design
Seamless integration with EasyStack Kubernetes Service, featuring unified quota management and a common network to ensure seamless business interoperability.
How it works
Architected on a mature lightweight virtualization stack and SDN, our secure container runtime provides granular isolation across multiple dimensions: securing untrusted applications, containing faults, guaranteeing performance, and isolating tenant networks.
Advantages
Why Choose EasyStack Secure Container Service?

Safety, Fault Isolation
Engineered for secure multi-tenancy, our container runtime isolates untrusted workloads and prevents lateral movement, ensuring that faults are isolated and host integrity is maintained.

Cloud resource network interworking
Our solution places secure containers within a unified cloud network. They operate natively alongside your compute and storage resources, with full access to vNICs, public IPs, and load balancers. This architecture eliminates network barriers, enabling effortless communication between containerized apps and existing cloud hosts.

Standard adaptation
It has the same user experience as ordinary containers in-network, log, monitoring, storage, and other aspects; it has the characteristics of an extremely fast startup, excellent compatibility, and stability.

Network isolation
Based on SDN network service, multi-tenant application network isolation capability is added to the secure container runtime.
Use cases
Use scenarios
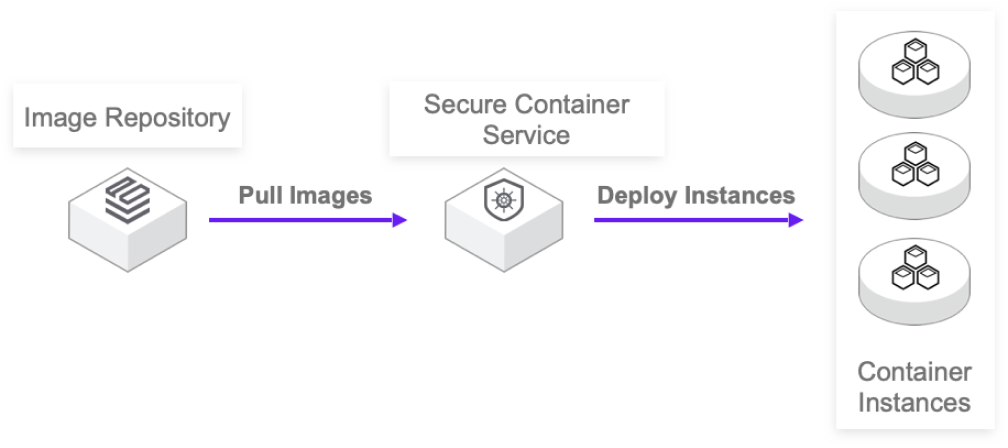
Modernize legacy virtual machine-based workloads
Traditional VMs offer robust security but miss out on the advantages of containerization and image-based workflows. They also come with significant overhead, minute-long provisioning times, and reliance on cumbersome VM images. Disparate networking setups further complicate delivery. Secure containers address these challenges by leveraging a lightweight VM-like isolation boundary, enabling startup times in seconds. They seamlessly integrate with your existing container platform, inheriting unified networking (CNI) and storage (CSI) solutions for streamlined operations.
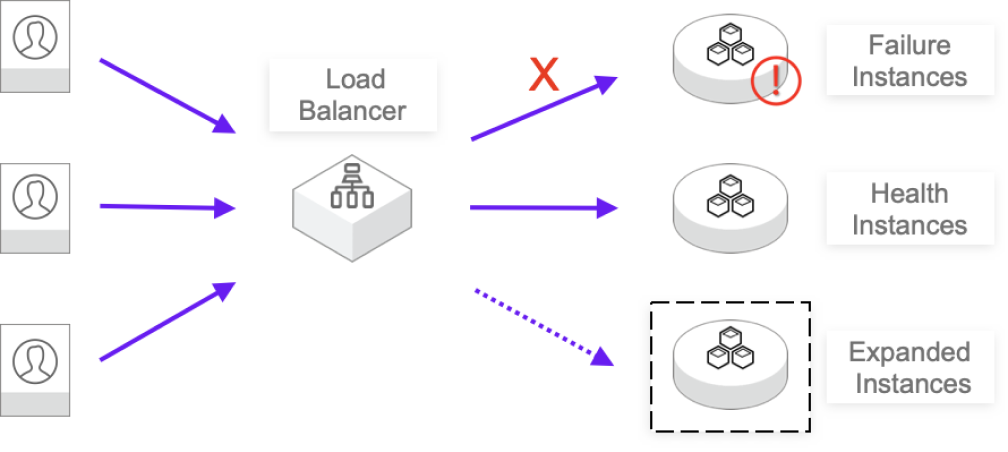
Untrusted Workload Isolation and Fault Isolation
In multi-tenant environments where containers share a kernel, a runtime or kernel flaw can be exploited to break out and bring down the entire host system. Secure containers are designed to eliminate this risk. By isolating untrusted workload and faults within a protected boundary, they ensure that a problem in one container cannot impact the host or other co-located workloads.
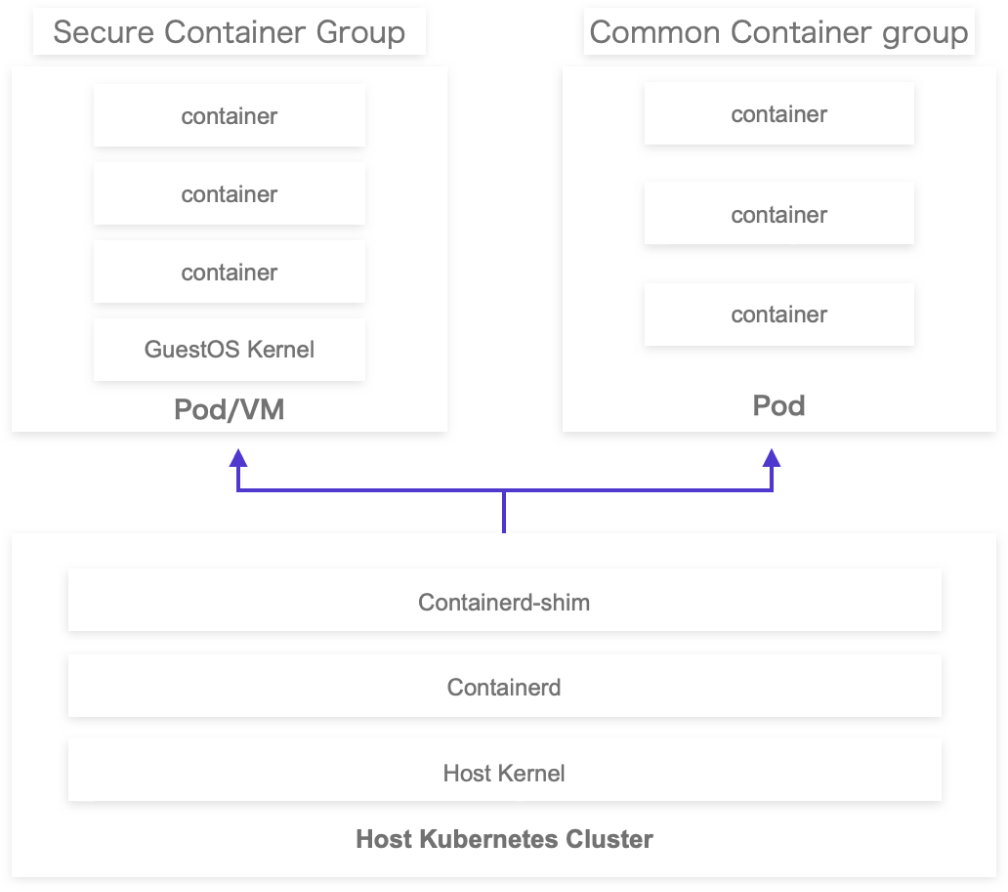
Dedicated Kernel per Application
Achieve strong isolation by running your application on its own exclusive OS kernel, ensuring superior security and stability.